View Secure Edge
The secure foundation for smart buildings
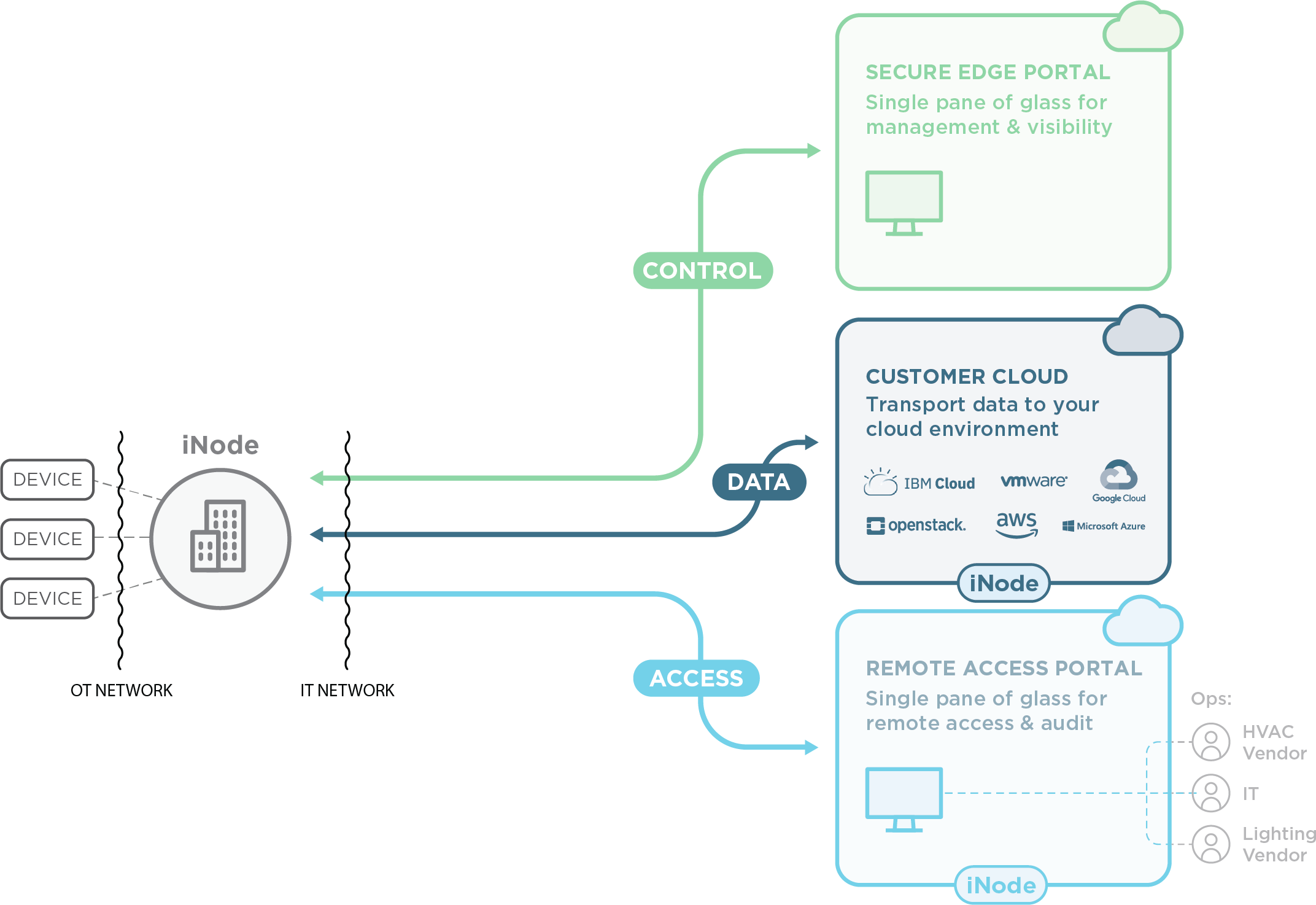
The View Secure EdgeTM plug-and-play solution enables IT teams to securely connect buildings to the cloud, secure building networks and devices, and deploy edge applications for real-time processing, insights, and optimizations.
Partner Marketplace
Accelerate your smart building transformation with turn-key deployments of industry leading applications and hardware.
Product Options
We have solutions for problems of any size, from small branch locations to large critical infrastructure.
Deployment & Hardware
Zero-touch deployment
Processor & Memory
Storage
Connectivity
Ports & Accessories
Security
Network & Device Management
Networks Supported
Intra-TAN Routing
Intra-site Routing
Supported NICs
Automated Device Discovery
Security Features
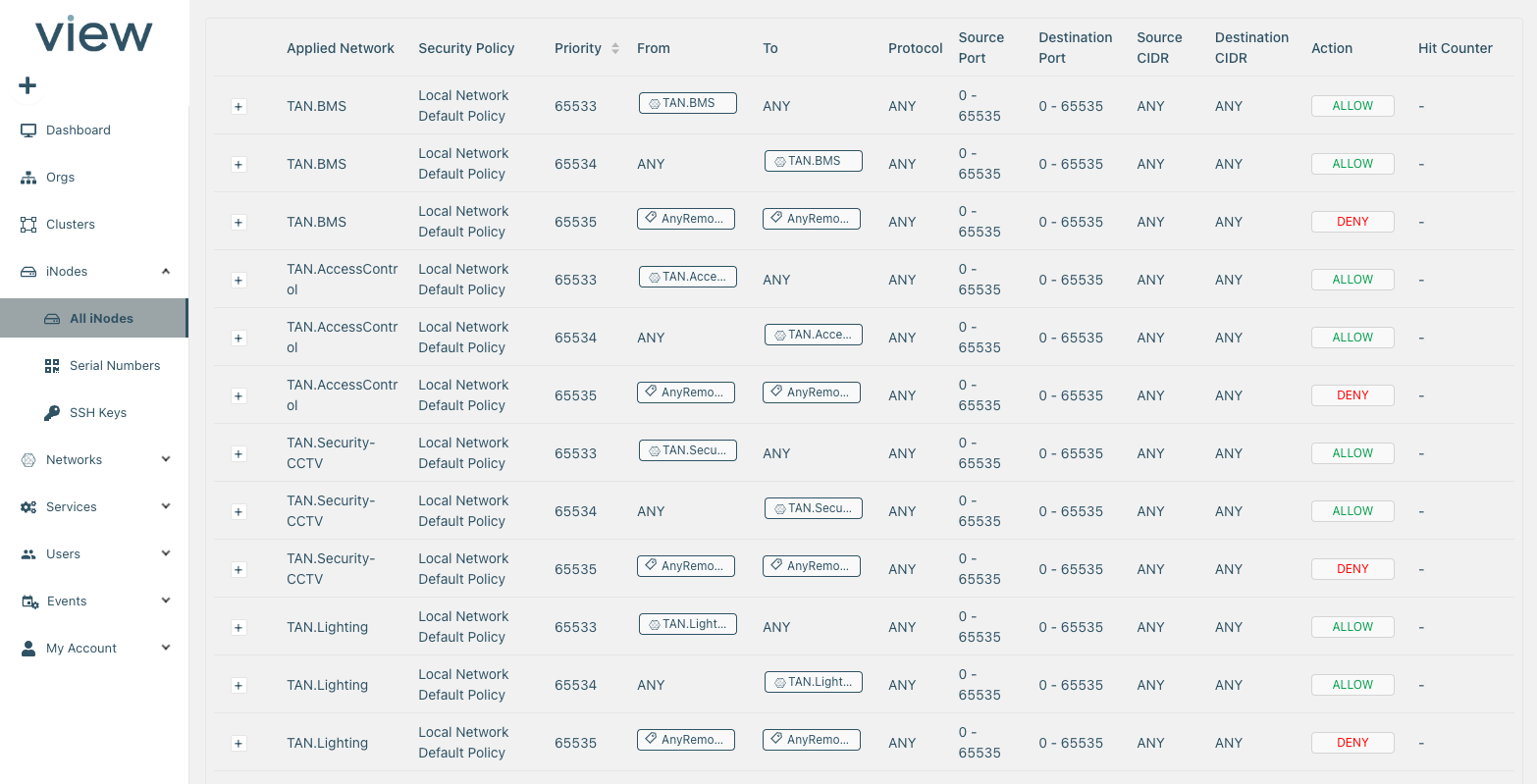
OT Firewall & Security Policies
Access Logs & Audit Trail
Alerting
Secure Tunnels
Continuous Threat Detection
Resiliency & High-Availablity
High-availability Configurations
Clustering
Multi-region Cloud Infrastructure
Remote User Access
Agentless Remote Access
Devices Supported
Legacy application support
SSO
Edge Compute
Cloud-managed edge applications
Core services (DHCP, SQL, NTP, etc.)
Services store with 3rd party services
Custom application deployment
Support & SLAs
99.5% uptime
99.999% uptime
Email & Web Support
Phone Support
Support Availability
Hardware Replacement SLA
Support SLA
Basic
Professional
0
Professional building infrastructure to secure complex networks with multiple devices and deploy edge applications.Enterprise
0
Enterprise-grade infrastructure with high-availability and resiliency to secure critical networks and deploy edge applications.